
An effective cybersecurity plan is imperative for any laboratory, given the often sensitive nature of the data it manages. However, a laboratory’s expertise lies in testing and analysis, not the vast and constantly evolving landscape of cyber risks. A cybersecurity standards framework can help labs develop a complete, effective, and affordable cybersecurity plan.
What are cybersecurity frameworks?
Cybersecurity frameworks consist of standards and guidelines that help organizations apply industry best practices to manage cybersecurity risks. Examples of cybersecurity frameworks include: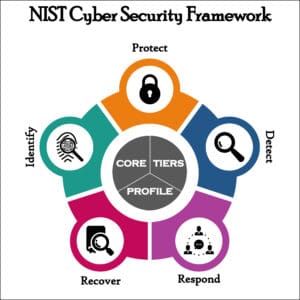
NIST Special Publication 800-53, Revision 5: Security and Privacy Controls for Information Systems and Organizations, is a mandatory framework for US federal agencies with highly granular guidance for implementing security controls.[1]
NIST Framework for Improving Critical Infrastructure Cybersecurity Version 1.1 (CSF) is a voluntary framework for state and local governments and private sector organizations that operate critical infrastructure.[2]
ISO/IEC 27002:2022 Information security, cybersecurity, and privacy protection — Information security controls is an international standard adopted by multinational corporations.[3]
What do frameworks mean by “appropriate” safeguards and activities?
Cybersecurity frameworks are general references that apply to organizations of any size, in different sectors, and with varying resources. As such, these documents recognize that a multi-billion dollar global corporation and a four-person startup must adopt different security practices.
Most frameworks maintain relevance to a broad audience by advising organizations to implement “appropriate” safeguards and activities.
What that means in practice will depend on the nature of a laboratory, its risk environment, and the risk tolerance of its leadership. Understanding how the lab’s context affects the design of each security control is essential to the cyber risk management process.
Benefits of cybersecurity frameworks to laboratories
Frameworks give laboratories at any scale access to best-practice approaches to managing cyber risks. Even without dedicated security experts, a lab’s information technology teams can use a framework document to address the full scope of modern cyber threats. Laboratories that rely on third-party IT vendors can use a framework to set requirements and monitor their vendors’ performance.
Certification of framework compliance can be good for business as it shows potential customers the lab’s commitment to security and the presence of comprehensive security controls. Customers are more likely to do business with framework-compliant labs.
Laboratories also use cybersecurity frameworks when selecting a laboratory information management system (LIMS) vendor. A LIMS collects, stores, and transmits a lab’s most sensitive data. As a result, the LIMS is central to implementing laboratory cybersecurity controls. LIMS vendors with accreditations to one or more security standards demonstrate their commitment to security best practices. They can also provide advice for developing an appropriate, framework-based cybersecurity plan.
LabLynx Cybersecurity
At LabLynx, our security plan is currently based on NIST 800-53 v4. Organizations must actively monitor management practices and controls, and take remedial action when significant deficiencies are encountered or improvements needed. We keep our server operating systems up to date with scheduled maintenance tasks, weekly reviews for vulnerabilities and periodic reviews of infrastructure.
Security and privacy controls are maintained such that our clients are capable of complying with their many security, privacy, and laboratory standards, frameworks and regulations. The hosted applications such as ELab are designed to be configurable to comply with your specific security requirements. Clients are capable of making many such configurations such as, but not limited to: users and profiles, access controls such as password complexity and history, session length, login info banners, and auditing of user account changes.
Information Security
LabLynx’s information security standard governs the security, protection, and handling of LabLynx information and records, and defines four broad information security classifications:
- Internal: Data is made available to internal company personnel as appropriate for their role.
- Public: Data is freely available to the public.
- Confidential: Access to data requires special qualifications or is covered by legal agreements. Examples include PII, PHI, the “special” GDPR categories, PCI-regulated data, data covered by NDAs, and so on.
- Restricted: Data that could lead to irreparable harm, criminal charges, or similar if accessed without Authorization.
Access to data must be restricted to users or information systems with a legitimate business need and authorized by the data owner or an authorized delegate of the owner. Authorization is on a need-to-know basis. Access is restricted to performing a specific job task. This requires that access is permissible to only the data, programs, or portions of the operating system to perform assigned functions or explicitly required for system functionality. Systems shall be configured to enforce access privileges based on job classification and function.
Data Sharing & Retention
LabLynx holds all client electronic data and records for at least 6 years unless directed otherwise. Clients can request adherence to their internal retention policy. Clients are responsible for providing such a policy upon agreement between both parties. LabLynx is responsible for data and records of clients that are hosted and maintained on LabLynx servers.
Access and Single Sign On
LabLynx offers single sign-on (SSO) via SAML. OpenSocial is built by LabLynx with the intention of handling SSO via SAML. For each organization that utilizes OpenSocial based SSO, a new instance of the application is created, manageable by the client.
Learn more about how LabLynx cybersecurity can help your lab
Laboratory security must be everyone’s concern, not just the IT department’s. Protecting laboratory data must be a continuous process rather than a discrete, one-time event. Integrating a LabLynx LIMS into your lab’s operations can dramatically improve lab security by providing a cybersecurity framework to ease the day to day security considerations.
LabLynx LIMS makes it easier to control access to data and laboratory systems and protect information shared within the lab without sacrificing productivity or collaboration.
Contact us today to learn more about enhancing laboratory security with a LabLynx LIMS solution.
References
- “NIST Special Publication 800-53, Revision 5: Security and Privacy Controls for Information Systems and Organizations 1”. National Institute of Standards and Technology 2023. Retrieved October 12, 2023. https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final
- “Cybersecurity Framework 1”. National Institute of Standards and Technology 2023. Retrieved October 12, 2023. https://www.nist.gov/cyberframework
- “ISO/IEC 27002:2022 Information security, cybersecurity and privacy protection — Information security controls 1”. International Organization of Standards 2022. Retrieved October 12, 2023. https://www.iso.org/standard/75652.html




